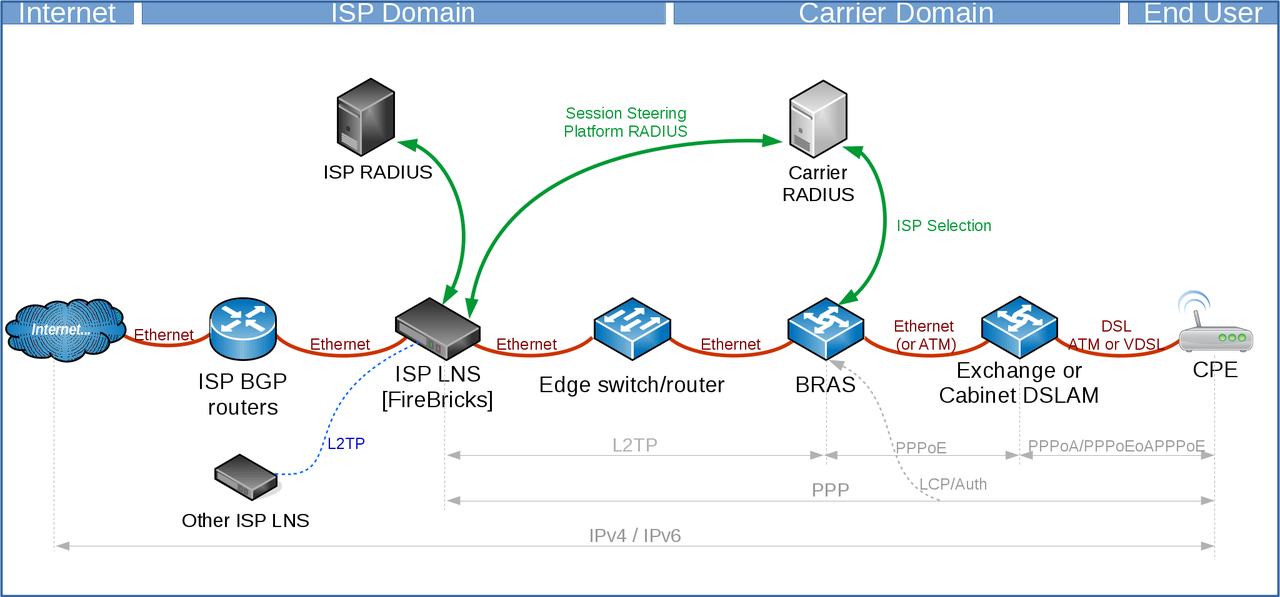
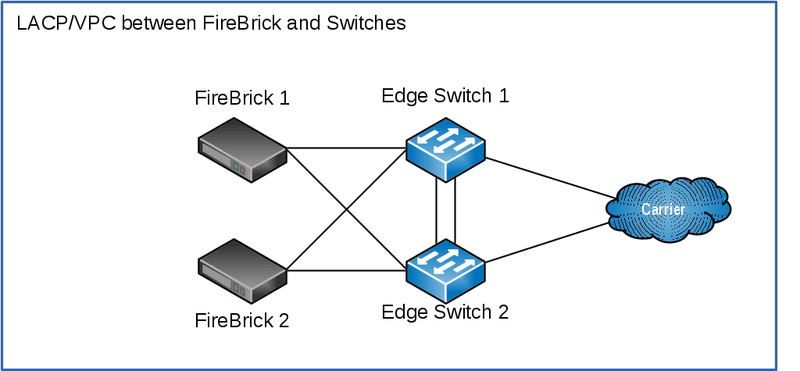
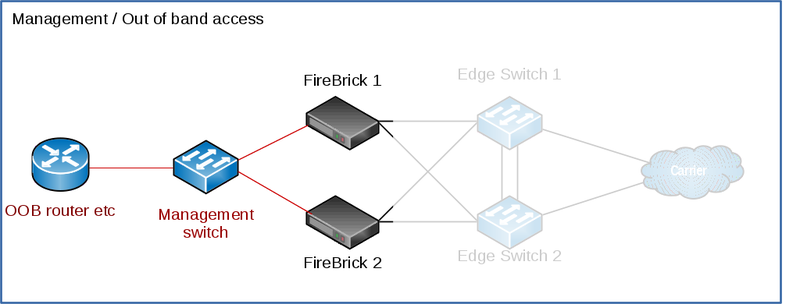
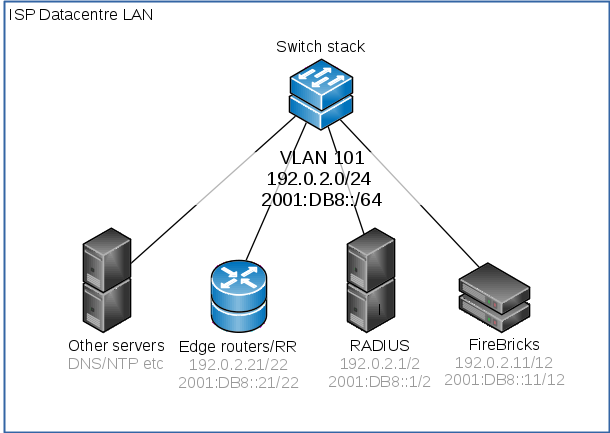
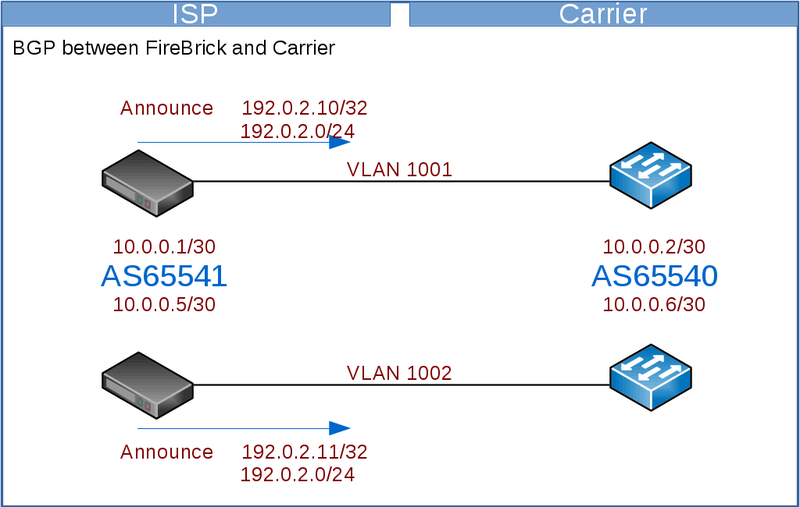
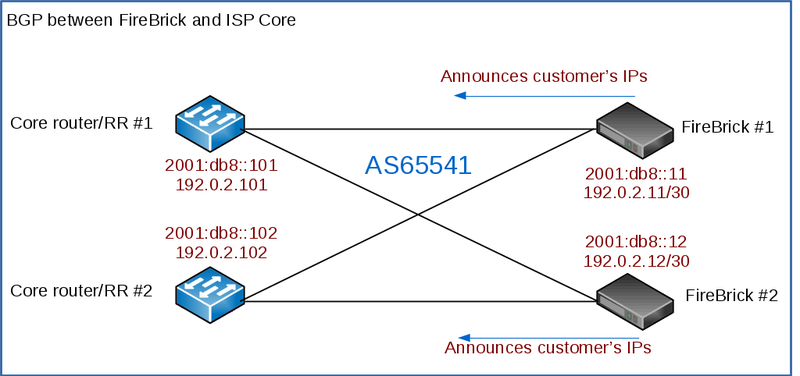
You will announce your LNS and RADIUS addresses to the carrier, typically you'd have a single BGP session per link to the carrier.
Here we will use the FireBrick to handle the BGP - we have two FireBricks and two interconnects to the carrier. You may prefer to run the BGP on a different device or devices according to your needs - eg if you have a larger number of FireBricks than the number of interconnects.
The carrier will announce their IPs to you - these vary between the carrier - eg, BT Wholesale will announce all their BRAS to you - which will be a large number, whilst TalkTalk only announce their a few IPs - which will be their LACs to you.
You will want to configure filters on the BGP connection to limit the prefixes accepted from the carrier or announced to the carrier, but be wary of the carrier increasing the number of prefixes with or without notifying you.
We will configure the interlink interface on a separate routing table. The FB6000 can have separate routing tables which act as completely separate internets. Using a separate table means you do not have to worry about what prefixes are announced on the BGP link as they will only apply to that routing table.
Whilst we would recommend using a BGP connection like this, if the carrier does not handle BGP then you will need static routes. Using a separate routing table can make this much simpler as you can set a default route to the carrier gateway on the interlink subnet.
When using a separate routing table, you have to take care to correctly configure the routing table on the interface, BGP, RADIUS, L2TP and loopback configuration elements.
TODO VRRP or LOOPBACKS HERE?
TODO RECOMMENDED FILTERS